OIDC Protocol
This content is adapted from Ping documentation.
What Is OIDC?
OpenID Connect (OIDC) is an open authentication protocol that works on top of the OAuth 2.0 framework. Targeted toward consumers, OIDC allows individuals to use single sign-on (SSO) to access relying party sites using OpenID Providers (OPs), such as an email provider or social network, to authenticate their identities. It provides the application or service with information about the user, the context of their authentication, and access to their profile information.
Why Use It?
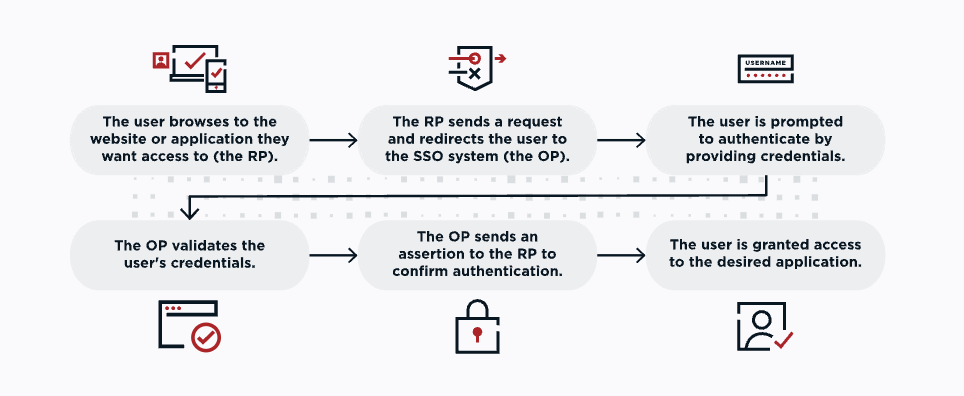
The purpose of OIDC is for users to provide one set of credentials and access multiple sites. Each time users sign on to an application or service using OIDC, they are redirected to their OP, where they authenticate and are then redirected back to the application or service.
OIDC is one of the newest security protocols and was designed to protect browser-based applications, APIs, and mobile native applications. It delegates user authentication to the service provider that hosts the user account and authorizes third-party applications to access the user’s account.
OIDC Real-World Example
There are currently two ways of creating a Spotify account:
- You can register with Spotify
- You can sign on through Facebook
Facebook sends your name and email address to Spotify, which uses that information to authenticate you.
You can experiment with an interactive OIDC flow with the official OpenID Connect Playground.
How Does OIDC Work?
OIDC is similar to OAuth where users give one application permission to access data in another application without having to provide their usernames and passwords. Instead, tokens are used to complete both authentication and authorization processes:
-
Identity tokens, intended to be read by the client, prove that users were authenticated and are JSON Web Tokens (JWTs), pronounced “jots.” These files contain information about the user, such as their usernames, when they attempted to sign on to the application or service, and the length of time they are allowed to access the online resources.
-
Access tokens are used to access protected resources, which are intended to be read and validated by the API. These tokens can be JWTs, but might be in a different format. Their purpose is to inform the API that the bearer of this token has been authorized to access the API and perform specific actions (as specified by the scope that has been granted).
ID tokens cannot be used for API access purposes and access tokens cannot be used for authentication.
OIDC Flow Diagram
SAML, OAuth, OpenID Connect
The primary difference between these standards is that OAuth, now known as OAuth 2.0, is an authorization framework used to protect specific resources, such as applications or sets of files, while SAML and OIDC are authentication protocols used to create secure sign-on experiences. SAML and OIDC are about who someone is, where OAuth is about what they are allowed to do.
OpenID Connect vs. OAuth
OAuth, now known as OAuth 2.0, is an open standard framework for API authorization. It defines how an API client can obtain security tokens that contain a set of permissions against the resources available through that API.
Instead of requiring a user to share login credentials with one application to give that application access to another, OAuth delegates authorization decisions to a separate authorization server that hosts the user account. Essentially, OAuth acts on behalf of the user, providing delegated access to a third-party service without the user exposing their credentials to that third party.
The primary difference between OpenID Connect and OAuth is that OAuth is an authorization framework used to protect specific resources, such as applications or sets of files, while SAML and OIDC are authentication standards used to create secure sign-on experiences.
SAML vs. OIDC
SAML and OIDC are both powerful authentication protocols used to create secure sign-on experiences, but are used for different purposes.
-
SAML is used to access browser-based applications and does not support SSO for mobile devices or provide API access. OAuth provides API access and OIDC provides access to APIs, mobile native applications, and browser-based applications.
-
SAML is known for its flexibility, but most developers find OIDC easier to use because it is less complicated.
-
SAML uses tokens written in XML and OIDC uses JWTs, which are portable and support a range of signature and encryption algorithms.